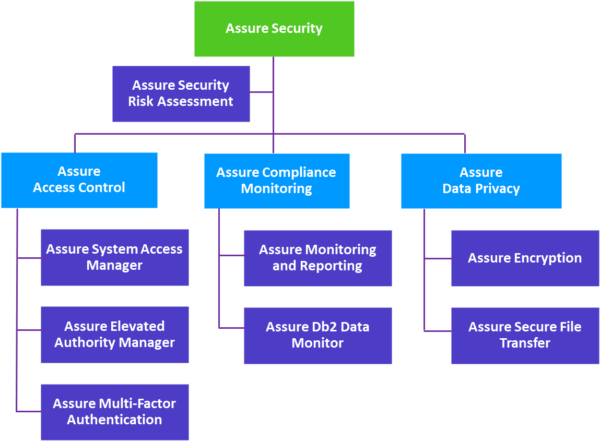
Assure Security
IBM i Security & Data Encryption
A comprehensive solution that addresses all aspects of IBM i security and helps to ensure compliance with cybersecurity regulations. Combined with Kantion’s experience in assessing security and implementing the appropriate solution, you benefit from pragmatic and cost effective answers to your requirements.
Whether your business needs to implement a full set of security capabilities, or you need to address a specific vulnerability, Assure Security is the solution.
Enabling your organisation to comply with cybersecurity regulations and strengthen IBM i security by controlling access to systems and data, enforcing data privacy, monitoring for compliance, and assessing risks.
- Detect and effectively addresses security breaches and compliance deviations quickly
- Protect the privacy of your company’s intellectual property, Personal Identifiable Information and prevent the theft of customer, partner and employee data
- Limit IBM i security threats by routinely assessing risks and taking control of logon security, powerful authorities, and system access
- Integrate your IBM i security monitoring with your enterprise SIEM strategy.
Each of the components of Assure Security can be purchased individually, so as to address areas of highest risk and priority first.
The Assure Security Risk Assessment is available free of charge and facilitates an efficient method to evaluate your current security measure with one of Kantion’s security consultants.