Assure Security
A comprehensive solution that addresses all aspects of IBM i security and helps to ensure compliance with cybersecurity regulations. Combined with Kantion’s experience in assessing security and implementing the appropriate solution, you benefit from pragmatic and cost effective answers to your requirements.
Whether your business needs to implement a full set of security capabilities, or you need to address a specific vulnerability, Assure Security is the solution.
Enabling your organization to comply with cybersecurity regulations and strengthen IBM i security by controlling access to systems and data, enforcing data privacy, monitoring for compliance, and assessing risks.
- Detect and effectively addresses security breaches and compliance deviations quickly
- Protect the privacy of your company’s intellectual property, Personal Identifiable Information and prevent the theft of customer, partner and employee data
- Limit IBM i security threats by routinely assessing risks and taking control of logon security, powerful authorities, and system access
- Integrate your IBM I security monitoring with your enterprise SIEM strategy.
Each of the components of Assure Security can be purchased individually, so as to address areas of highest risk and priority first.
The Assure Security Risk Assessment is available free of charge and facilitates an efficient method to evaluate your current security measure with one of Kantion’s security consultants.
Compatible Platforms
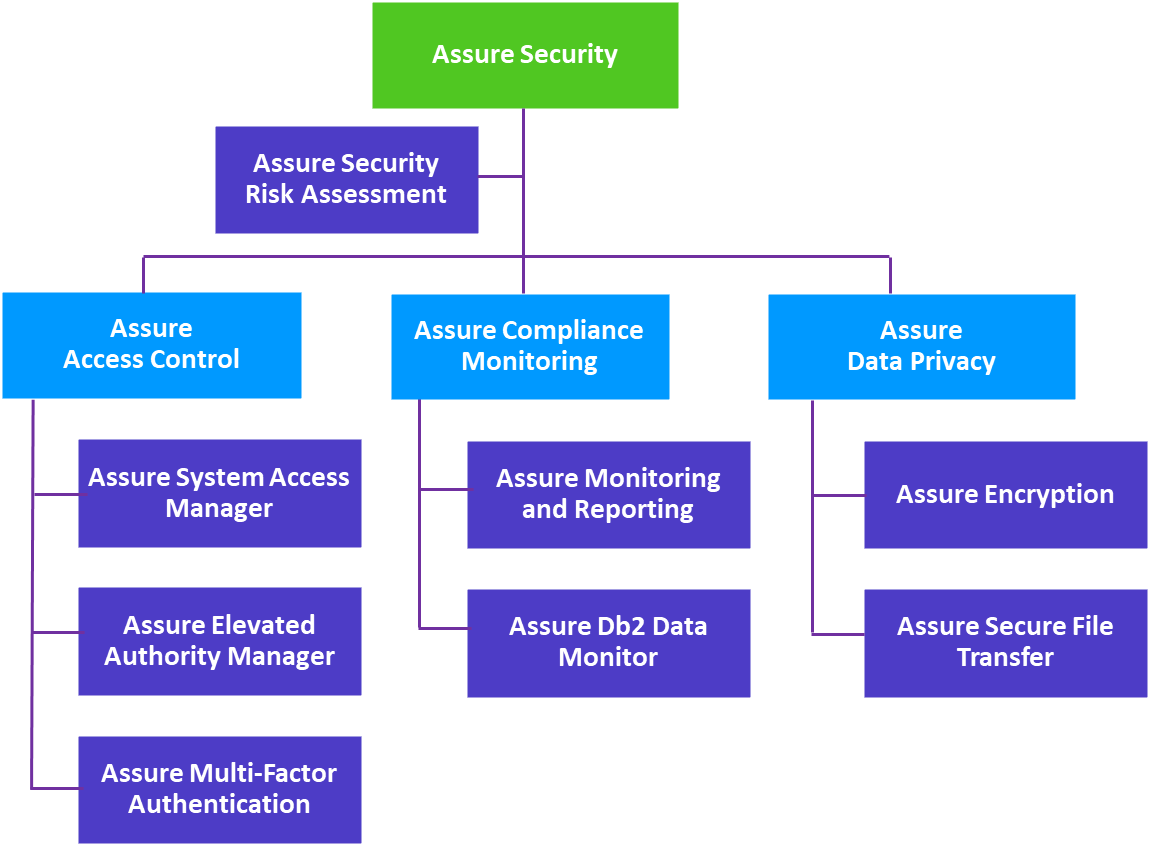
Components of Assure Security
Assure Security Risk Assessment
Assure Security Risk Assessment provides a useful and informative picture of your IBM i security. Reports can be given to IT risk and compliance auditors help fulfill requirements for an annual risk assessment required under regulations such as PCI DSS and HIPAA. The tool can be re-run at any time without burdening IT staff.
Assure System Access Manager primarily uses exit point technology to detect access attempts to your IBM i systems and data, determine whether to accept or deny them, and optionally log those decisions and trigger actions.
Assure Elevated Authority Manager
With Assure Elevated Authority Manager, when a user needs additional authority for a specific action, they ask for elevation of authority within their job. That request must specify a profile with the authority needed and the command to be run. Requests can be accepted by the administrator, or when configured to automatically grant requests, rules defined by the administrator are consulted to determine whether the request should be granted.
Assure Multi-Factor Authentication
When integrated with the signon screen, Assure Multi-Factor Authentication enables you to choose between single-step or two-step authentication. Single step authentication requires both the user’s password and a token for authentication. The user is not told which one failed if either is incorrect, delivering true multi-factor authentication. With the two-step process, a token screen is presented after the IBM i signon.
Assure Monitoring and Reporting
Comprehensively monitors system and database activity to save you time and money on achieving regulatory compliance, identifying compliance deviations and detecting unauthorized activities on IBM i systems.
Gives you complete control over the visibility of confidential IBM i data. It monitors and alerts you to users who have viewed sensitive records in Db2 databases, as well as how and when the data was viewed. It even blocks records from view by unauthorized users.
Protects sensitive data at-rest from unauthorized access using the only NIST-certified AES encryption for IBM i. Optimized for performance, Assure Encryption easily automates encryption and decryption of Db2 data, including database fields, backup tapes, Save files, IFS files and more, with built-in masking and access auditing. To keep encryption keys secure, Assure Encryption supports FIPS 140-2 compliant Alliance Key Manager from Townsend Security as well as other OASIS KMIP-compliant key management solutions. Assure Encryption also provides extensive tokenization capabilities to temporarily or permanently replace confidential information on your server with token values.
IBM i customers need to meet regulatory requirements to secure the transfer of data over the Internet and on internal networks. Assure Secure File Transfer provides secure FTP (SFTP) and Secure Shell (SSH) transfer support to meet these regulations. Additionally, PGP Command Line 9 encryption is available as an added option.
Benefits of Assure Security
-
Achieve and maintain compliance with the cybersecurity requirements of GDPR, PCI DSS, HIPAA, SOX and other state and industry regulations.
-
Protect your company’s intellectual property and the data of customers, partners and employees from theft.
-
Quickly detect and effectively address security incidents and compliance deviations.
-
Automate common security and compliance management tasks.
-
Comprehensively monitor system and database activity.
-
Prevent unauthorized access to IBM i systems and data.
-
Ensure the privacy of confidential data both at-rest and in-motion.
-
Provide real segregation of duties.
-
Implement security best practices.
